ABOUT YLI
YLI Electronic is one of the most professional electric locks manufacturers in Asia. We have strong R&D skills, production capacities and distribution channels. Our products are Magnetic locks, Strike lock, Dropbolt, Keypad,Buttons,Door holder, remote control and other accessories ,totally over 600 types of products. Our Shenzhen factory and Eping factory are covering an area of 30,000 square meters…
More
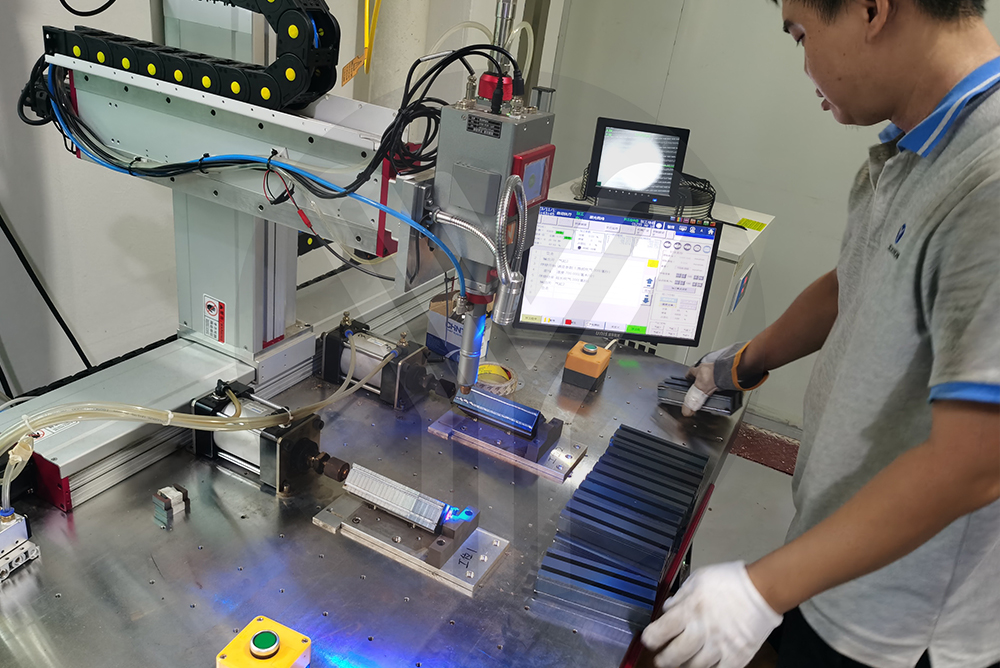
Our factory
WHY CHOOSE US
News
CERTIFICATE
FQA
Frequently Asked Questions
A: 3 years for Magnetic Lock, 2 years for electric bolt and 1 year for rest items。
A: 100PCS for OEM
A: T/T, western union
A: Sample order: 1-3 working days
Bulk order: 7-15 working days
A:Free samples are not available
A:We are the biggest mabufacturer in China
A: More than 20 years
A:Check whether the power supply is normal ,the power LED is on (Red light),whether the Circuit board is damaged.
A:check whether the body surface of magnetic lock and adjust the armature plate is appressed,or try to adjust the looseness of armature plate,or check if the Current and voltage is sufficient
A: (a) Check if the POWER SUPPLY output is reduced,”Current,Voltage”:1A/12V/24V
(b) Check if there are foreign objects on the surface of magnetic body(like Rust, dirt ,debris and etc.)
A: (a) Check whether there has installed the Shock absorption gasket
(b) Check the armature plate ,if the screw loose
(c) Check whether the distance between the main body of magnetic lock and armature plate is appropriate